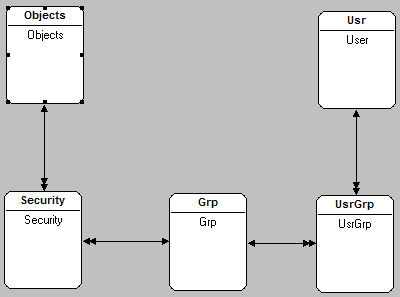
Objects
Objects are screens, reports, query screens and other programs. You can assign specific security access to each object.
You can get a list of the object names that are in the menus by going to the menu option Security/Menus and then click on the link “Print”. This list contains all the menus, the name and description of each object.
You can also see the name of the objects between square brackets in the window title of each form or in the upper left hand corner of reports.
Users
You should define a user for each person in the company that uses the InStyle Software™ system. Each user is assigned a set of groups that he or she belongs to.
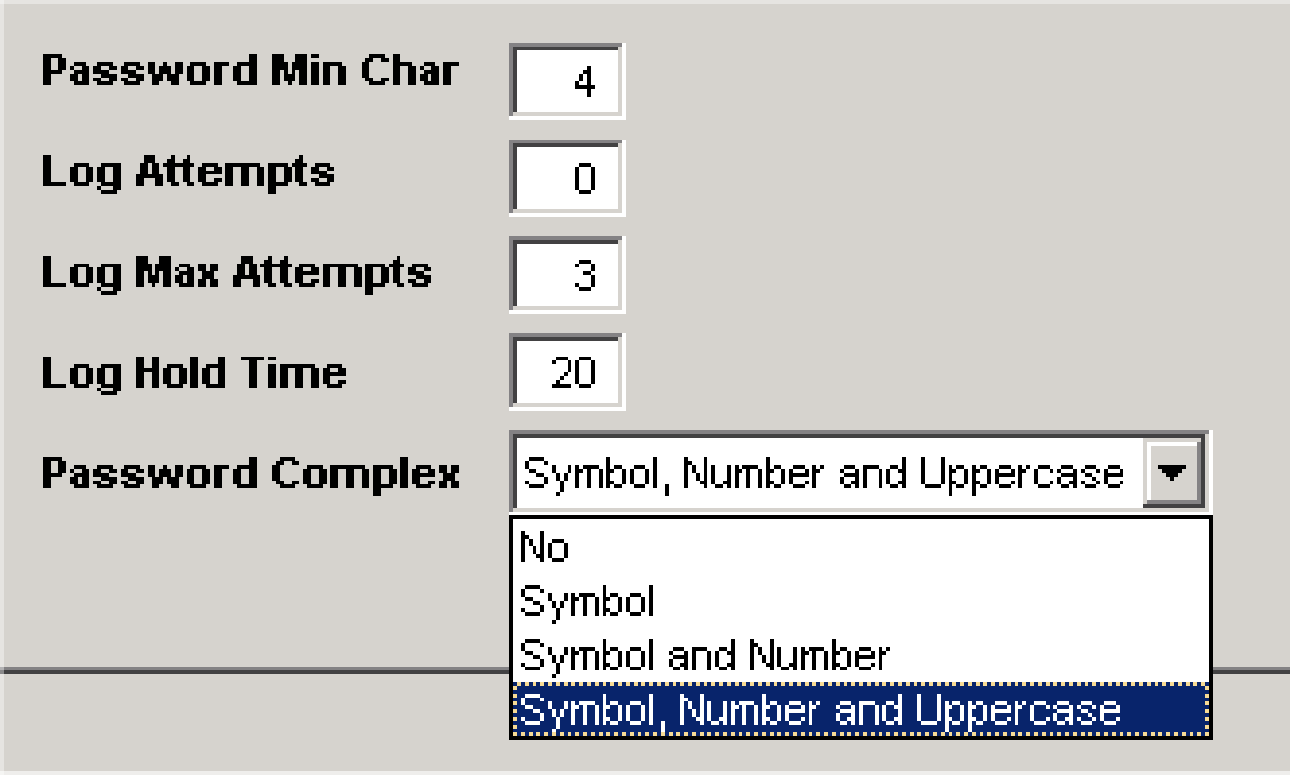
If the Login for the user fails more than Max Log Attempts, the system will create a wait/hold time for the login based on the hold time. The user will need to wait this length of time before another attempt can be made at logging in. To release a user immediately, change the log attempts to 0.
If Password Complex is changed from “No” to any other option, and the password is not changed, the user will have to enter their password in all caps.
New passwords are saved in the case that the password is entered, except when the option Password Complex is “No”, they are saved in uppercase.